The rise of hybrid working and the constant innovation of attack vectors creates many unpleasant surprises for IT security professionals. More than ever, a new approach is needed to secure the future of work.
Network Access Control, or NAC, provides the mechanism for ensuring only authenticated users can access the private company network. Once granted access, NAC enforces policies to regulate the areas of the network users can access while continuously monitoring and logging their activity.
NAC solutions automatically detect devices as they connect from either inside or outside to the network and then verify they are not compromising the security in place. As an important part of a Zero Trust, NAC enables IT admin to control network on-boarding and the access to network resources as well as the devices connected to it, even those we don't know.
NAC follows the Principle of the 3 A’s:
.png?width=2528&height=1896&name=NAC%20%E2%80%93%203%20Principles%20(1).png)

The primary goal of NAC is to keep unknown and unauthorized users from accessing a private company network. The uplift in demand for Network Access Control is a response to:
Utilised by many of the world’s leading companies since 2001, Soliton has been market leader in Network Access Control since then. Listening to our customers we designed an all-in-one NAC solution taking away the complexity and frustration of network access control.
Granular control for both users and guests for time-limited and secure access to encrypted (free) Wi-Fi
Agentless providing role- and device-based secure network access control for any device, employees, contractors and guests across any multi-vendor wired, wireless and VPN infrastructure
From 100 up to 100,000 devices
Initial set up takes less than 5 minutes, full NAC is up and running in 30 minutes (depending on infrastructure)
By using industry-standard authentication technologies, NetAttest EPS avoids vendor lock-in issues and provides easy integration with third-party products

Soliton's approach is always to take out complexity and enable easy control and management for IT. The wizard-guided feature of NetAttest EPS allows a quick, intuitive dashboard making it straightforward to install and maintain.
Soliton developed a unified deployment process to distribute and install digital certificates on any device. The multiplatform certificate management app (Soliton KeyManager) means the deployment process is always the same - regardless of device or operating systems.
The Soliton KeyManager app makes it easy for network administrators to use short-life certificates for enhanced security. With the application users can self-service on any device, automatically requesting and installing user- and device certificates in just 3 steps. Soliton KeyManager app also sends users a warning when certificates are due to expire. Users simply click the link to renew the certificate.
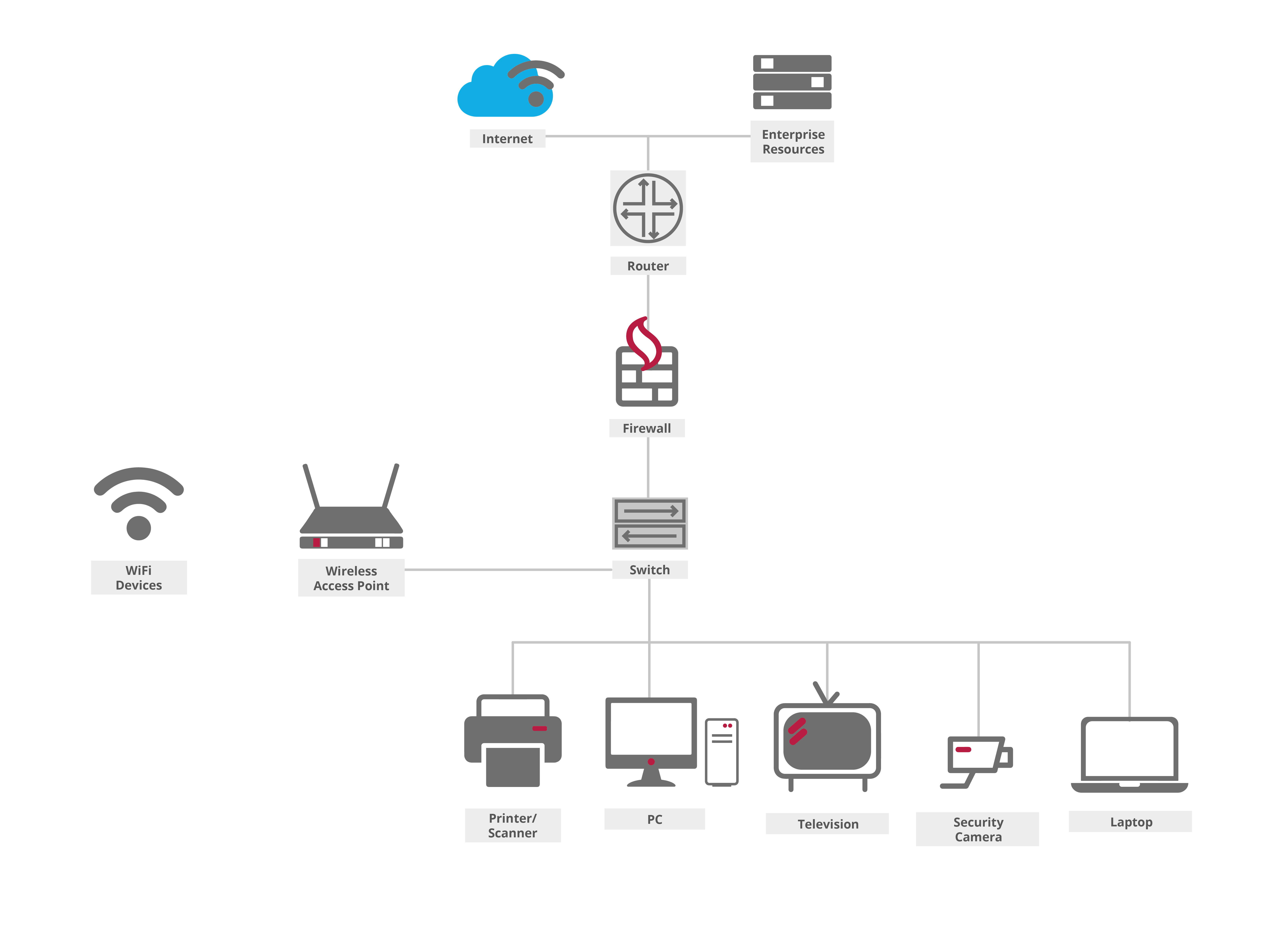
Soliton relies on the fundamental IEEE 802.1X framework at the heart of our NAC solution. This framework exemplifies our dedication to enhancing network security, fortifying against potential threats. Discover its strength within network access control, enhancing defence mechanisms and user experiences alike. Explore how IEEE 802.1X advances network integrity.
In our development processes, we aim to create solutions that not only support the CEO/CISO and the IT manager, perhaps even more important the end-users too. All our solutions take out complexity and enable easy control and management.

Return on Investment (ROI)
Regulatory Compliance

Operational efficiency

Easy technology that frees people up to work anytime, anywhere.
Adapting to the modern world and shifted level of expectations to access company networks from any location using any device. Each device creates a vulnerability that could make it possible for cyber criminals to get around traditional security controls. A NAC solution is inevitable to handle permissions and authentication of unknown devices attempting to access the network.
Understanding the different use cases for our NAC technology:
More employees are working remotely and take their own devices to work and use them for work purposes.
The use of IoT devices continues to grow and employees expect to use them for work purposes.
Contractors, partners, or temporary workers need to access the company network. NAC provides access privileges and prevents unauthorized access to certain parts of the network while guest users experience smooth connectivity.
NAC solution provides ease in managing all the permissions that are needed for specific segments of the network.
The growing reliance on the Internet of Medical Things (IoMT) devices plus healthcare being a highly regulated industry, NAC is a must.
NAC off-load tasks from IT and Help Desk to increase their productivity.